Reach out to our team or give us a call, and we’ll be happy to help you secure your business’s digital landscape.
As a Managed Service Provider (MSP) and Managed Security Service Provider (MSSP) for Glen Oaks Dentistry, BastionX has led the management and security of their infrastructure for over a decade. Our longstanding partnership includes expertly managing two major infrastructure upgrades, adding advanced security to protect sensitive data and operations. Additionally, we offer ongoing helpdesk support, ensuring Glen Oaks Dentistry enjoys seamless, uninterrupted services. Our dedication to excellence and proactive adaptation to new technologies highlight our commitment to Glen Oaks Dentistry’s continued success and security.

Zero Trust (ZT)
At BastionX, the Zero Trust security model is integral to our framework. As well as permeating every aspect of our product and service offerings. Additionally, we incorporate strict identity verification, least privilege access, and micro-segmentation strategies across our entire suite. This ensures that every transaction and interaction within your network is continuously validated. While embedding Zero Trust principles into the core of our solutions, we deliver robust protection. Not to mention, stringent policy enforcement that adapts to the evolving security landscape.
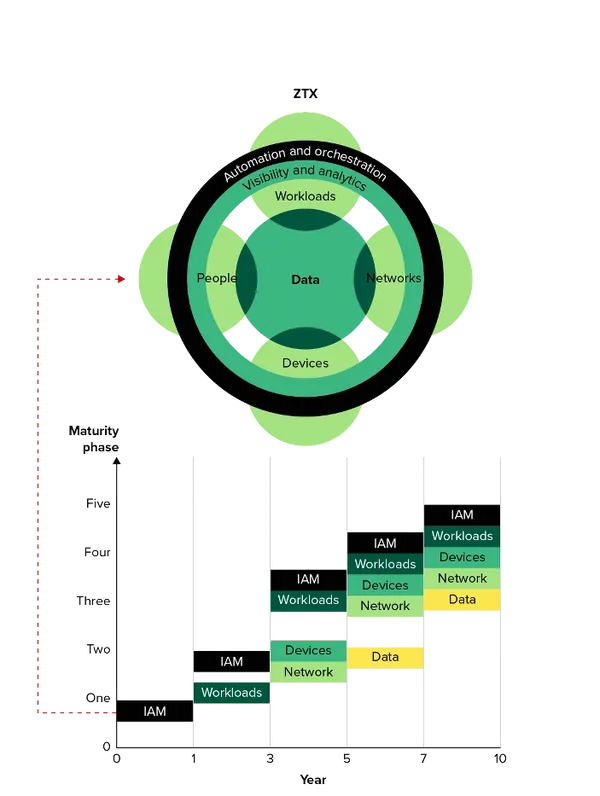
BastionX’s cybersecurity approach is perfectly attuned to the Zero Trust eXtended (ZTX) framework, as illustrated in the provided image. Our solutions encompass comprehensive protection across people, data, networks, workloads, and devices, with a steadfast commitment to identity and access management (IAM). We incorporate advanced automation, orchestration, and analytics to ensure our Zero Trust enforcement. Making sure it’s not only rigorous but also intelligent and responsive to the dynamics of the cybersecurity landscape. Your organizations trust should never assumed, but continuously earned and verified.
OUR EXPERTISE
- Network security: ZTNA alternatives to VPN, secure gateways for your workforce
- Cloud and application protection
- Device security and posture management
- IAM, PAM, and ZT for your clients and workforce
- Our experts adhere to the highest security standards. Even the most rigid organizations such as NIST, and CIS establish our Zero Trust principles
- Nonetheless, regardless of your current security posture, our engineers can assist you in achieving 100% ZT adoption.
Benefits:
- Enhanced Security Posture: We adopt a Zero Trust approach. BastionX ensures that every access request is fully authenticated, authorized, and encrypted. While significantly reducing the risk of data breaches and unauthorized access.
- Continuous Verification: The model incorporates continuous validation of all transactions and interactions within your network. This ensures that security is not a one-time check but an ongoing process.
- Least Privilege Access: BastionX enforces the principle of least privilege. This grants users and devices the minimum level of access necessary to perform their functions. Therefore minimizing the potential impact of a security breach.
- Micro-Segmentation: Additionally, we segment the network into smaller, secure zones. BastionX’s Zero Trust model limits lateral movement within the network, making it more difficult for attackers to navigate and access sensitive information.
- Adaptive Security Policies: BastionX’s solutions are designed to adapt to the evolving security landscape. With our stringent policy enforcement, that adjusts to new threats and vulnerabilities.
- Comprehensive Protection: The Zero Trust eXtended (ZTX) framework ensures protection across all key areas. This includes people, data, networks, workloads, and devices.
- Robust Identity and Access Management (IAM): A strong focus on IAM ensures that only authorized users and devices can access your network and resources. While further enhancing security.
- Advanced Automation and Orchestration: BastionX incorporates automation and orchestration to streamline security processes, making Zero Trust enforcement more efficient and effective.
- Intelligent Analytics: The use of advanced analytics helps in identifying and responding to security threats in real-time, ensuring that your organization’s security posture is proactive rather than reactive.
- Trust Verification: In a Zero Trust model, trust is never assumed but continuously earned and verified, fostering a more secure and trustworthy environment within your organization.
While implementing BastionX’s Zero Trust security model, organizations can achieve a more secure, agile, and responsive cybersecurity posture, capable of adapting to the ever-changing threat landscape.
